File Sharing - managing file access
This article explains, how to control who can access shared files on a Windows PC connected to the College network or on a shared storage service such as a NAS. It is useful for anyone who needs to manage shared folders for their team.
To keep things easy to manage, try to create new folders that need different access permissions as close to the main (top-level) folder as possible—ideally just one level below it. Avoid creating many layers of sub-folders, as this can make permission settings more complicated.
This approach makes it easier when you need to add or remove people or change who can see or edit certain folders. Whenever possible, use existing AD (Active Directory) groups, or create a new group, to manage permissions. This keeps everything simpler and more organised.
Understanding NTFS permissions
If you want to securely share files from your computer or if you are managing a Network Attached Storage (NAS) folder, you will need to be familiar with NTFS permissions as you will be responsible for setting and periodically checking the security permissions of the shared files or NAS and conducting regular reviews of the folder permissions. NTFS is currently the preferred file system used in Windows environment. This allows you to control which users and groups can access files and folders on an NTFS file system.
Standard NTFS permissions
The table below explains the meaning of available permission settings.
Once you set the relevant permission level, based on the steps below, it is advisable that you check with the user that it matches what they can actually access.
Permission |
Meaning for Folders |
Meaning for Files |
Read |
Permits viewing and listing of files and subfolders |
Permits viewing or accessing of the file's contents |
Write |
Permits adding of files and subfolders |
Permits writing to a file |
Read & Execute |
Permits viewing and listing of files and subfolders as well as executing of files; inherited by files and folders |
Permits viewing and accessing of the file's contents as well as executing of the file |
List Folder Contents |
Permits viewing and listing of files and subfolders as well as executing of files; inherited by folders only |
n/a |
Modify |
Permits reading and writing of files and subfolders; allows deletion of the folder |
Permits reading and writing of the file; allows deletion of the file |
Full Control |
Permits reading, writing, changing, and deleting of files and subfolders |
Permits reading, writing, changing and deleting of the file |
How to set permissions
- Right-click on the folder whose permissions you wish to change, and click on Properties.
- Select the Security tab.
- Click Edit.
- Click Add.
- Enter the relevant username or group name and click Check Names. If the name is valid, it should become underlined. Click OK.
Note that some permission groups e.g. for an entire department, are updated automatically based on HR records when new staff start or exiting staff leave. However, other custom permission groups are not automatically updated and require a request to be sent to IT Services to have the new staff member added or an older staff member removed. If you need clarification about any group and whether the membership is automatically updated please contact the IT Service Desk.
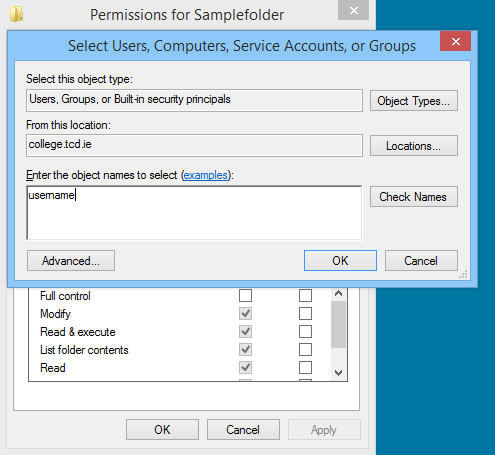
- Select the required permissions and click OK
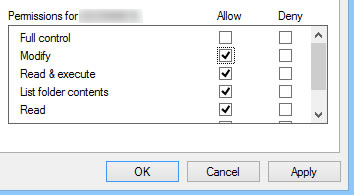
- Repeat steps 5-7 for all relevant users and user groups. Do not remove the listing for Domain Admins.
Understanding Inheritance
By default, objects within a folder inherit the permissions from that folder when the objects are created. However, explicit permissions take precedence over inherited permissions. So, if you grant different permissions at a lower level, the lower level permissions take precedence.
When you view the permissions, they will be one of the following
- Checked: Permissions are explicitly assigned.
- Cleared (unchecked): No permissions are assigned.
- Shaded: Permissions are granted through inheritance from a parent folder.
Disabling inheritance for a group
To remove permissions inheritance for a group, you must turn off the option for inheriting permissions and then remove the group in security tab.
To disable inheritance for a group
- Right-click the file or folder and select Properties.
- Select the Security tab.
- Click the Advanced button.
- Click the Permissions tab.
- Click Change Permissions.
- Deselect Include inheritable permissions from this object's parent.
- Click Add to convert inherited permissions to explicit permissions.
- Click OK, click OK again.
- You can now remove group permissions as per how to set permissions above, but do not remove the listing for Domain Admins
Denying access
Besides granting the Allow permissions, you can also grant the Deny permission. The Deny permission always overrides the permissions that have been granted.
Inherited vs effective permissions
Because a person can belong to several groups, they might receive different permission settings for the same file or folder. When this happens, Windows combines all these permissions to decide what the person can actually do.
These final permissions are called effective permissions. They include both the permissions that were set directly for the user or group (explicit permissions) and any permissions that were passed down from the folders above (inherited permissions).
Checking who has effective permissions
To view the NTFS effective permissions
- Right-click the file or folder and select Properties.
- Select the Security tab.
- Click the Advanced button.
- Click the Effective Permissions tab.
- Click Select, type the name of the user or group you want to view. Click OK.

